VoIP testing involves different angles, most importantly performance tests, functional tests, but also security tests. Now there is something in for the launch of Sipfront:
Sipfront teams up with Enable Security to offer SIPVicious Pro scenarios!
If you expose a VoIP system to the public internet, you might notice within a couple of minutes certain strange SIP traffic patterns trickling in. The advanced SIP engineer will immediately know what’s up: SIPVicious, also known as friendly-scanner, has found your box and is trying to find a hole in our system by checking for weak passwords.
The best defense against such attacks is taking initiative and pro-actively check your VoIP system against weak spots. This is done by putting several measures in place:
- rate-limit requests per source IP;
- block user agents trying to authenticate against a valid or invalid extension for too many times in a row;
- check in public databases for known fraudsters e.g. by using the fantastic API Ban service;
- enforce strong password policies to prevent dictionary attacks
Last but not least, actively verify your system by running security checks against them!
Our latest partner Enable Security is the author of SIPVicious and their commercial version [SIPVicious PRO] (https://www.sipvicious.pro/). They are true experts in the field of Penetration Testing and Fuzzing. Based on this partnership, we’re now able to provide you with highly efficient offensive security test scenarios based on their tools with the click of a button!
What’s SIPVicious PRO?
SIPVicious PRO is a professional-grade security testing suite built from the experience of the folks of Enable Security. Their aim is to help vendors and operators of VoIP systems to build and deploy products that withstand attack.

SIPVicious PRO provides a large range of test scenarios, among them being:
- SIP INVITE Flood
- SIP Digest Leak
- SIP INVITE enumeration
- RTP Bleed and Injection attack
- Online and offline password cracking of SIP credentials
- and more…
How is Sipfront leveraging SIPVicious PRO?
Over the course of the next months, we will gradually make more and more security tests available to the Private Beta and Enterprise plans.
Making these kind of tests available to the public will come hand in hand with tightened target validation processes within Sipfront. In order to run certain security tests against a target host, you will have to validate that target via DNS and/or via specific SIP users we’d ask you to create on the system in order to check if you have the authority over the System under Test to avoid abuse.
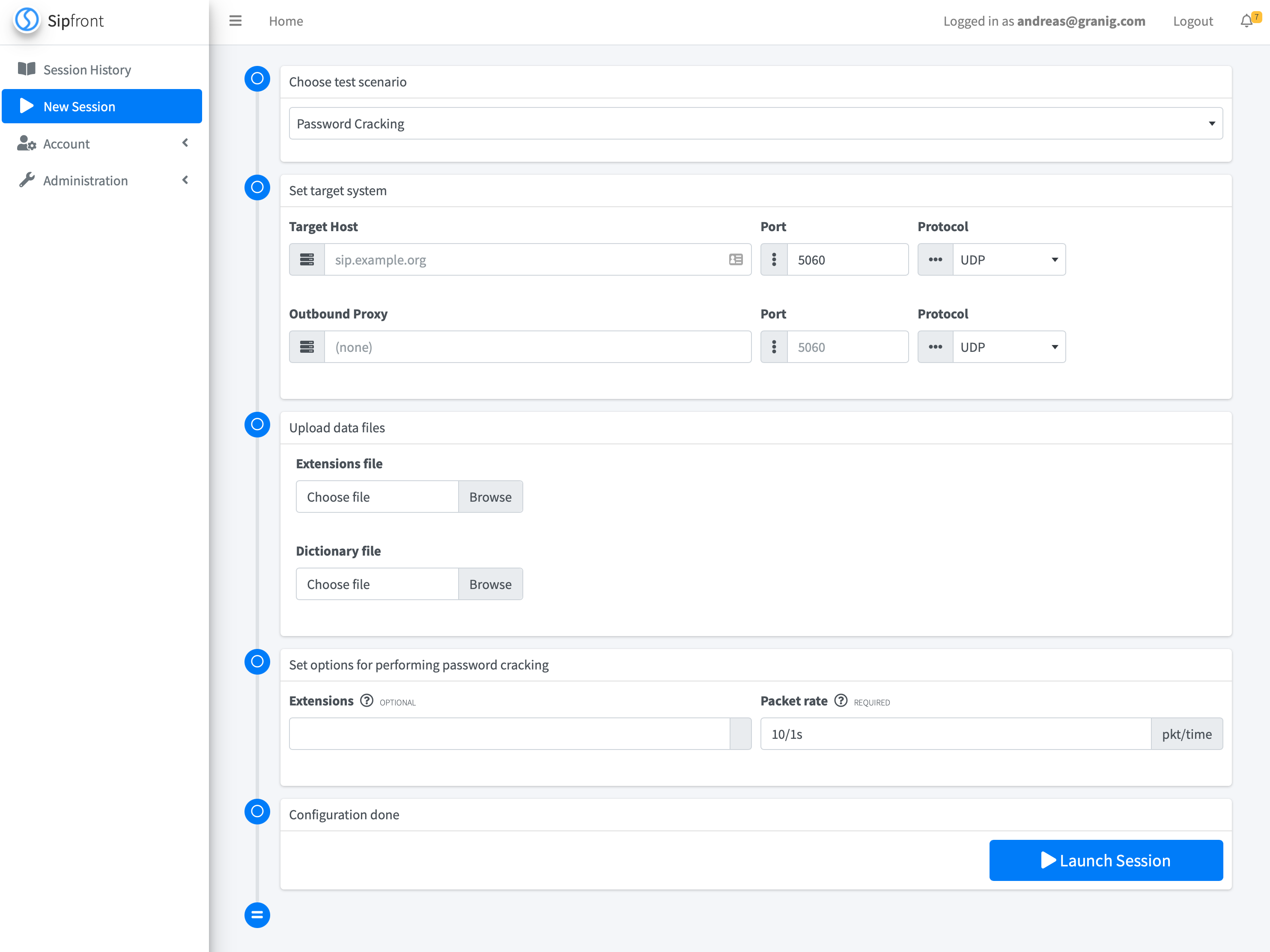
Show, don’t tell!
Check the following 50 seconds video to see a SIP online password cracking session powered by SIPVicious PRO.
The result is presented in raw format for now.
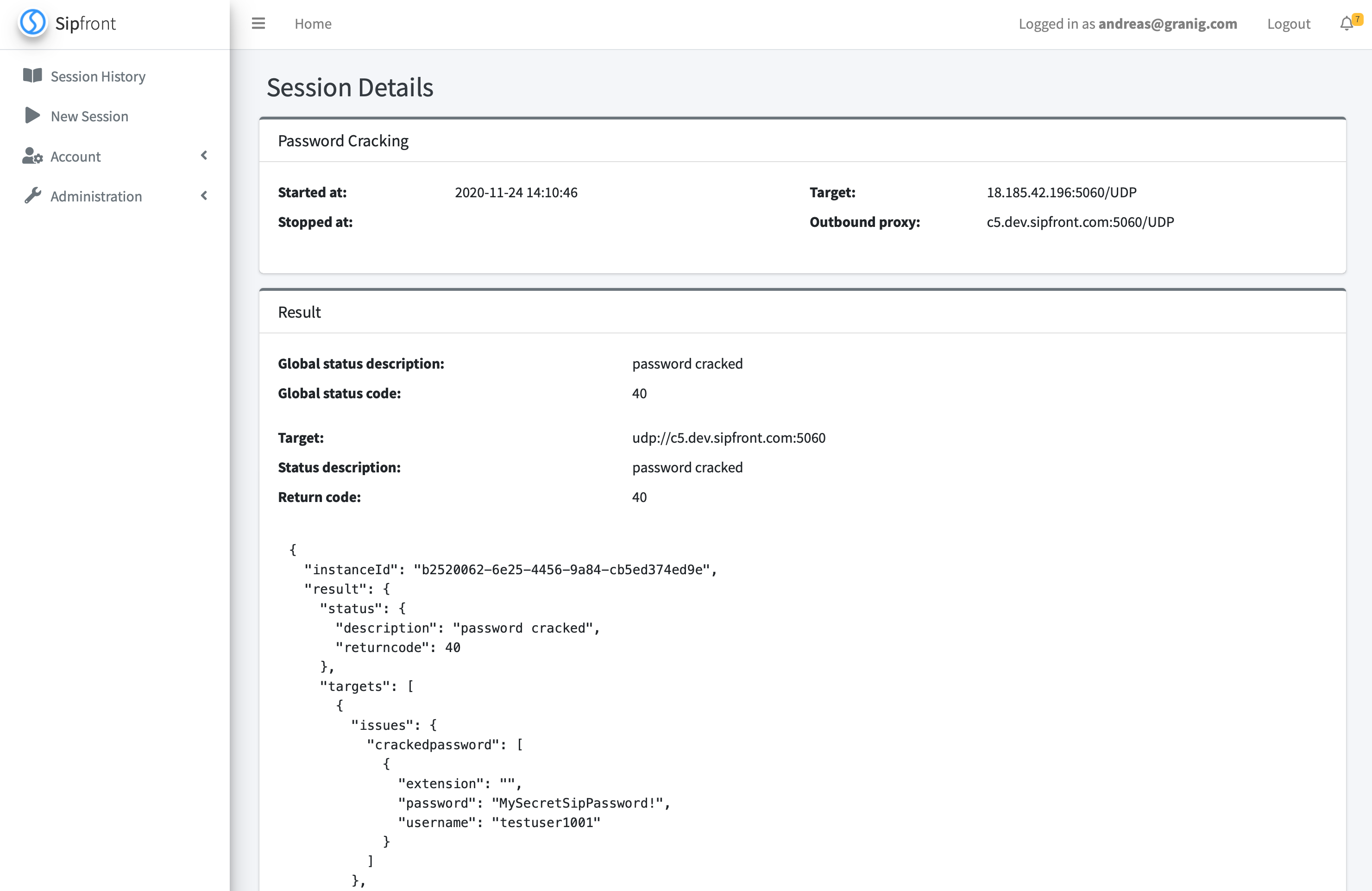
I sincerely hope, this new feature is going to be valuable as another tool in your SIP testing belt to enhance the security and resilience of your deployments.
comments powered by Disqus